목차
( 제가 작업했던 프로젝트 코드 기반으로 설명하고 있습니다.)
1. build gradle 에 의존성 추가
//시큐리티 버전은 스프링버전에 따라 사용방법이 완전히 다릅니다. //시큐리티 5버전 => 스프링 부트 2버전 (수업) //시큐리티 6버전 => 스프링 부트 3버전 (문법이 완전 변경되니 주의) implementation 'org.springframework.boot:spring-boot-starter-security' //시큐리티 타임리프에서 사용 implementation 'org.thymeleaf.extras:thymeleaf-extras-springsecurity5' //시큐리티 테스트 testImplementation 'org.springframework.security:spring-security-test'
- 시큐리티가 처음 설정 되면 모든 요청에 대해서 시큐리가 기본 제공하는 로그인 화면이 보이게 됨.
- 기본아이디는 user / 비밀번호는 console창에 비밀번호를 발급됨.
- 로그아웃의 경로는 /logout이 기본이 된다.
2. 시큐리티 설정 파일 구현
security_config.java

주요메서드

3. SecurityConfig 에 SecurityFilterChain 구현
package com.project.tobe.config; import com.project.tobe.dto.UserRole; import org.springframework.context.annotation.Bean; import org.springframework.context.annotation.Configuration; import org.springframework.security.config.annotation.web.builders.HttpSecurity; import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity; import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder; import org.springframework.security.web.SecurityFilterChain; @Configuration @EnableWebSecurity //시큐리티 설정파일을 시큐리티 필터에 등록 public class SecurityConfig { @Bean public BCryptPasswordEncoder encoder() { return new BCryptPasswordEncoder(); // 비밀번호 암호화를 위한 인코더 } @Bean public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception { http .csrf().disable()//csrf토큰 사용x .authorizeRequests() // 인증 및 권한 부여 규칙 설정 .antMatchers("/login.user").permitAll() // 로그인 페이지는 인증 없이 접근 허용 .antMatchers("/employee.do").hasAnyRole("S", "A") // "/employee.do" 경로는 "A","S" 역할을 가진 사용자만 접근 가능 .antMatchers("/*.do").authenticated() // ".do"로 끝나는 모든 요청은 인증된 사용자만 접근 가능 .anyRequest().permitAll() // 그외 요청은 인증 없이 접근 가능 .and() .formLogin() // 로그인 설정 .loginPage("/login.user") // 로그인 페이지 설정(사용자 정의) .usernameParameter("employeeId") //로그인폼에서 아이디필드 name 값을 employeeId 로 설정 .passwordParameter("employeePw") //로그인폼에서 비밀번호필드 name 값을 employeePw 로 설정 .loginProcessingUrl("/loginForm") //로그인 페이지를 가로채 시큐리티가 제공하는 클래스로 로그인을 연결 .defaultSuccessUrl("/main.do") //로그인 성공 시 이동할 URL .failureUrl("/login.user?err=true") // 로그인 실패시 이동 URL // .failureHandler(new CustomAuthenticationFailureHandler()) // 커스텀 실패 핸들러 등록 .and() .logout() // 로그아웃 설정 .logoutUrl("/logout") // 로그아웃 페이지 설정 .logoutSuccessUrl("/login.user") // 로그아웃 성공 시 이동할 URL .invalidateHttpSession(true)// 로그아웃 시 세션 무효화 .deleteCookies("JSESSIONID") // 로그아웃 시 쿠키 삭제 (JSESSIONID) .and() .exceptionHandling() //인증(Authentication) 또는 권한 부여(Authorization) 관련 예외 처리 .accessDeniedPage("/accessDenied"); //접근권한이 없는 요청은 accessDenied 페이지로 이동 return http.build(); } }

해당 형태를 시큐리티에게 전달해야하기 때문에 객체 구현을 먼저해줘야한다.
4. UserDetailsService 구현 (인증객체 만들기)

package com.project.tobe.serviceimpl; import com.project.tobe.entity.Employee; import com.project.tobe.repository.EmployeeRepository; //import com.project.tobe.security.EmployeeDetails; import com.project.tobe.security.EmployeeDetails; import lombok.RequiredArgsConstructor; import org.springframework.security.core.userdetails.UserDetails; import org.springframework.security.core.userdetails.UserDetailsService; import org.springframework.security.core.userdetails.UsernameNotFoundException; import org.springframework.stereotype.Service; @Service @RequiredArgsConstructor //loginProcessingUrl()가 호출되면 loadUserByUsername이 자동 호출됨 public class PrincipalDetailsService implements UserDetailsService { private final EmployeeRepository employeeRepository; /** * 사용자의 아이디(username)를 통해 인증 정보를 로드하는 메서드입니다. * 스프링 시큐리티에서 로그인 요청 시 호출됩니다. */ @Override public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException { // 데이터베이스에서 username을 기준으로 Employee 객체 조회 Employee employee = employeeRepository.findById(username) .orElseThrow(() -> { // username 에 해당하는 사용자가 없으면 예외 발생 return new UsernameNotFoundException("해당 유저를 찾을 수 없습니다."); }); // 조회된 사용자 객체를 EmployeeDetails (유저 객체) 로 변환하여 반환 // 시큐리티세션( new Authentication(new MyUserDetails()) ) 형식으로 전달 됨 return new EmployeeDetails(employee); } }
5.UserDetails 구현 (유저 객체 만들기)
package com.project.tobe.security; import com.project.tobe.dto.EmployeeDTO; import com.project.tobe.entity.Employee; import com.project.tobe.dto.UserRole; import org.springframework.security.core.GrantedAuthority; import org.springframework.security.core.authority.SimpleGrantedAuthority; import org.springframework.security.core.userdetails.UserDetails; import java.util.ArrayList; import java.util.Collection; public class EmployeeDetails implements UserDetails { private Employee employee; private EmployeeDTO employeedto; public EmployeeDetails(Employee employee) { this.employee = employee; } // 권한 관련 작업을 하기 위한 role return @Override public Collection<? extends GrantedAuthority> getAuthorities() { Collection<GrantedAuthority> authorities = new ArrayList<>(); try { UserRole role = UserRole.valueOf(employee.getAuthorityGrade()); // authorityGrade를 UserRole Enum으로 변환 authorities.add(new SimpleGrantedAuthority("ROLE_" + role.name())); // ROLE_ 접두사 붙이기 } catch (IllegalArgumentException e) { // authorityGrade 값이 UserRole Enum에 정의되어 있지 않은 경우의 처리 System.err.println("Invalid authorityGrade value: " + employee.getAuthorityGrade()); } return authorities; } // get Password 메서드 @Override public String getPassword() { return employee.getEmployeePw(); } // get Username 메서드 (생성한 User은 loginId 사용) @Override public String getUsername() { return employee.getEmployeeId(); } public String getNickname() { System.out.println(employee.toString()); System.out.println(employee.getEmployeeName()); return employee.getEmployeeName(); } public String getUserAuthorityGrade() { return employee.getAuthorityGrade(); } // public String getUserAuthorityName() { // System.out.println(employeedto.getAuthorityName()); // return employeedto.getAuthorityName(); // } // 계정이 만료 되었는지 (true: 만료X) @Override public boolean isAccountNonExpired() { return true; } // 계정이 잠겼는지 (true: 잠기지 않음) @Override public boolean isAccountNonLocked() { return true; } // 비밀번호가 만료되었는지 (true: 만료X) @Override public boolean isCredentialsNonExpired() { return true; } // 계정이 활성화(사용가능)인지 (true: 활성화) @Override public boolean isEnabled() { return true; } }
6. 인증 객체 정보 가져오기
컨트롤러
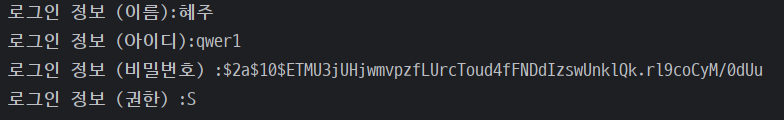
//현재 로그인 정보 가져오기 @GetMapping("/user-info") public ResponseEntity<?> employeeUserInfo(Authentication authentication) { if (authentication == null) { // 인증 객체가 없다면 return ResponseEntity.status(HttpStatus.UNAUTHORIZED).body("Unauthorized"); } //인증객체 안에 principal값을 얻으면 유저객체가 나옴 EmployeeDetails user = (EmployeeDetails)authentication.getPrincipal(); System.out.println("로그인 정보 (이름):" + user.getNickname()); System.out.println("로그인 정보 (아이디):" + user.getUsername()); System.out.println("로그인 정보 (비밀번호) :" + user.getPassword()); System.out.println("로그인 정보 (권한) :" + user.getUserAuthorityGrade()); // 사용자 이름과 권한을 반환 Map<String, Object> response = new HashMap<>(); response.put("userName", user.getNickname()); response.put("userId", user.getUsername()); response.put("userPw", user.getPassword()); response.put("userAuthorityGrade", user.getUserAuthorityGrade()); return ResponseEntity.ok(response); }
view (타임리프)
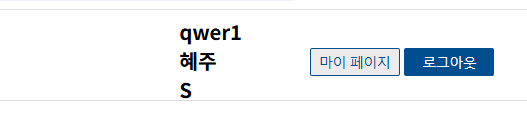
<html xmlns:th="http://www.thymeleaf.org" xmlns:sec="http://www.thymeleaf.org/extras/spring-security"> . . . <!-- 인증 되었다면 true, 아니면 false를 반환합니다. if문처럼 사용됩니다. --> <div sec:authorize="isAuthenticated()"> <span>[[${#authentication.principal.getUsername}]]</span><br/> <span>[[${#authentication.principal.getNickname}]]</span><br/> <span>[[${#authentication.principal.getUserAuthorityGrade}]]</span><br/> </div>
view (리액트)
useEffect(() => { const fetchUserId = async () => { try { const response = await axios.get('/employee/user-info'); console.log("인증된 사용자 정보" + response.data); } catch (error) { console.error("Error fetching user ID:", error); } }; fetchUserId(); }, []);

7. 세션 - 쿠키 방식


